If you’re looking for enhancing the protection and defense against malicious attacks and hacking, consider Enhanced Mitigation Experience Toolkit (EMET), a free utility provided by Microsoft which is mainly meant for enterprise users. EMET helps to detect and block exploitation techniques that are commonly used to exploit memory corruption vulnerabilities, and prevent vulnerabilities in software from being successfully exploited.
Enhanced Mitigation Experience Toolkit (EMET) allows developers and administrators to harden programs and prevent hackers from gaining access to the system through arbitrary applications, especially through zero-day exploit and common vulnerabilities, including the infamous exploit existed in Adobe Acrobat PDF Reader products.
EMET anticipates the most common actions and techniques adversaries might use in compromising a computer, and helps protect by diverting, terminating, blocking, and invalidating those actions and techniques through various security mitigation technologies. These technologies function as special protections and obstacles that an exploit author must defeat to exploit software vulnerabilities. Although these security mitigation technologies do not guarantee that vulnerabilities cannot be exploited. However, they work to make exploitation as difficult as possible to perform. Thus, EMET helps protect your computer systems even before new and undiscovered threats are formally addressed by security updates and antimalware software.
EMET also provides a configurable SSL/TLS certificate pinning feature that is called Certificate Trust. This feature is intended to detect (and stop, with EMET 5.0) man-in-the-middle attacks that are leveraging the public key infrastructure (PKI).
Enhanced Mitigation Experience Toolkit, as its name implied, is a security mitigation technologies, and are designed to make it more difficult for an attacker to exploit vulnerabilities in a given piece of software. EMET allows users to manage these technologies on their system and provides several unique benefits:
- No source code needed: Until now, several of the available mitigations (such as Data Execution Prevention) have required for an application to be manually opted in and recompiled. EMET changes this by allowing a user to opt in applications without recompilation. This is especially handy for deploying mitigations on software that was written before the mitigations were available and when source code is not available.
- Highly configurable: EMET provides a higher degree of granularity by allowing mitigations to be individually applied on a per process basis. There is no need to enable an entire product or suite of applications. This is helpful in situations where a process is not compatible with a particular mitigation technology. When that happens, a user can simply turn that mitigation off for that process.
- Helps harden legacy applications: It’s not uncommon to have a hard dependency on old legacy software that cannot easily be rewritten and needs to be phased out slowly. Unfortunately, this can easily pose a security risk as legacy software is notorious for having security vulnerabilities. While the real solution to this is migrating away from the legacy software, EMET can help manage the risk while this is occurring by making it harder to hackers to exploit vulnerabilities in the legacy software.
- Ease of use: The policy for system wide mitigations can be seen and configured with EMET’s graphical user interface. There is no need to locate up and decipher registry keys or run platform dependent utilities. With EMET you can adjust setting with a single consistent interface regardless of the underlying platform.
- Ongoing improvement: EMET is a living tool designed to be updated as new mitigation technologies become available. This provides a chance for users to try out and benefit from cutting edge mitigations. The release cycle for EMET is also not tied to any product. EMET updates can be made dynamically as soon as new mitigations are ready.
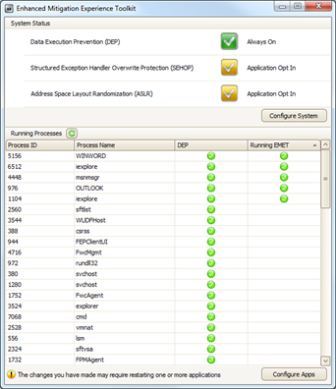
The EMET toolkit supports both 32-bit and 64-bit applications, and activates 14 pseudo mitigation technologies aimed at disrupting current exploit techniques on compiled binaries that does not have such mitigation mechanisms. The security mitigations complement other defense in-depth security measures, such as Windows Defender and antivirus software. EMET installs with default protection profiles, which are XML files that contain preconfigured settings for common Microsoft and third-party applications. Some of the mitigation techniques include:
- Attack Surface Reduction (ASR) Mitigation
- Export Address Table Access Filtering (EAF+) – This mitigation is designed to break nearly all shell code in use today. Before a piece of shellcode can do anything useful, it generally has to locate windows APIs first. EAT protects against metaspoilt shell codes by filtering access to the EAT (Export Address Table) of kernel32.dll and ntdll.dll through hardware breakpoints to block access if the instruction pointer is not inside a module.
- Dynamic Data Execution Prevention (Dynamic DEP) locks parts of memory used by process as non-executable, making it difficult to exploit memory corruption vulnerabilities.
- Structured Error Handling Overwrite Protection (SEHOP) perform SEH (Structured Exception Handling) chain validation to prevent exploit to overwrite SEH.
- NullPage Allocation Security Mitigation allocates the first page of memory before program initialization and blocks attackers from taking advantage of NULL references in usermode.
- Heap Spray Allocation blocks the use of pre-allocation memory addresses by malicious exploits to place copies of their shellcode in waiting for making a case to take control of instruction pointer.
- Export Address Table Filtering (EAF) Security Mitigation
- Mandatory address space layout randomization (ASLR), as well as non-ASLR-aware modules on Windows Vista, Windows Server 2008 and Windows 7 or later so that DLL loads executable code in random different memory locations each time it is called, making exploit code that target buffer overflows or other vulnerabilities hard to predict where the shell code is. The problem with this is that all modules have to use a compile time flag to opt into this. With EMET, modules are forced to be loaded at randomized addresses for a target process regardless of the flags it was compiled with
- Bottom Up ASLR Security Mitigation
- Load Library Check – Return Oriented Programming (ROP) Security Mitigation
- Memory Protection Check – Return Oriented Programming (ROP) Security Mitigation
- Caller Checks – Return Oriented Programming (ROP) Security Mitigation
- Simulate Execution Flow – Return Oriented Programming (ROP) Security Mitigation
- Stack Pivot – Return Oriented Programming (ROP) Security Mitigation
These pseudo mitigations are not robust enough to stop future exploit techniques, but can help prevent users from being compromised by many of the exploits currently in use. For example, ASLR on Adobe Reader and Adobe Acrobat DLL file named icucnv36.dll will patch the security hole of the Adobe PDF zero-day exploit. The mitigations are also designed so that they can be easily updated as attackers start using new exploit techniques.
The Enhanced Mitigation Experience Toolkit has been evolved to version 2.0, and interested administrators or users can download the EMET 2.0 from Microsoft Download Center.
What’s the differences of EMET and DEP (Data Execution Prevention)? EMET does not replace DEP, but uses DEP as one of the security mitigation technologies. In other words, EMET, if configured, forces applications to use several security defenses built into Windows, including Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP). As such, the settings of DEP depends on EMET.
Enhanced Mitigation Experience Toolkit must be configured after installation, or else it won’t do anything. Enterprise IT professionals can easily deploy EMET through Microsoft System Center Configuration Manager and apply Group Policies in Windows Active Directory to comply with enterprise account, user, and role policies. Administrators can customize and configure EMET deployments and determine which applications they want to protect through which mitigation techniques.
EMET supports Windows 7, Windows 8, Windows 8.1, Windows Server 2003 Service Pack 1, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Vista Service Pack 1, and Windows XP Service Pack 3.
Download Enhanced Mitigation Experience Toolkit from Microsoft Download Center:
EMET v5.2 (not for Windows XP)
EMET v4.1 Update 1
Also available is EMET user guide and EMET training video, which can also be viewed below.
Recent Posts
- Able2Extract Professional 11 Review – A Powerful PDF Tool
- How to Install Windows 10 & Windows 8.1 with Local Account (Bypass Microsoft Account Sign In)
- How to Upgrade CentOS/Red Hat/Fedora Linux Kernel (cPanel WHM)
- How to Install Popcorn Time Movies & TV Shows Streaming App on iOS (iPhone & iPad) With No Jailbreak
- Stream & Watch Free Torrent Movies & TV Series on iOS with Movie Box (No Jailbreak)
 Tip and Trick
Tip and Trick
- How To Download HBO Shows On iPhone, iPad Through Apple TV App
- Windows 10 Insider Preview Build 19025 (20H1) for PC Official Available for Insiders in Fast Ring – Here’s What’s News, Fixes, and Enhancement Changelog
- Kaspersky Total Security 2020 Free Download With License Serial Key
- Steganos Privacy Suite 19 Free Download With Genuine License Key
- Zemana AntiMalware Premium Free Download For Limited Time